There’s a brief announcement on the Adobe Product Security Incident Response Team (PSIRT) Blog stating that Adobe is looking into reports of a new exploit for their Reader software. No further details are provided. Since this exploit is apparently being seen in the wild, we recommend extreme caution when opening PDF documents from unknown or untrusted sources. Better yet, switch to a different PDF reader like Foxit, thereby avoiding the dangers inherent in using Adobe Reader.
Update: Ars Technica has the details. Apparently the vulnerability was reported by the security company FireEye, and attacks based on the vulnerability have been seem in the wild. Further, the vulnerability is important because security in version 11 of the Reader software was supposedly much more difficult to circumvent.
Update 2: There’s a new post on the Security Advisory blog for Adobe Reader and Acrobat that covers this issue.
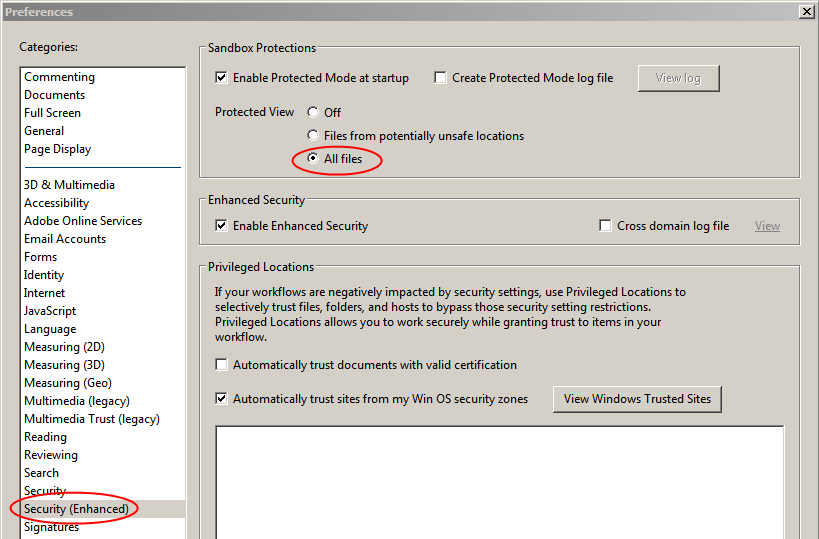
Update 3: Ars Technica points out that Adobe Reader 11 would protect users from this vulnerability, if its security settings were actually enabled by default (which they aren’t). On learning this, I immediately made the required changes to my installation of Reader, enabling Protected View. Check the bottom of this post for the procedure.
Update 4: Adobe announced that updates for the vulnerabilities in Reader will be made available some time during the coming week.
Enabling Protected View in Adobe Reader 11
- Start Adobe Reader.
- From the menu, select Edit > Preferences.
- Select Security (Enhanced) from the list on the left.
- In the Sandbox Protections section at the top, make sure that the setting for Protected View is All files.
- Click OK.
 boot13
boot13