 Security professionals have been saying it for years. The specific dangers associated with email have changed during that time, but the advice remains valid, and applies to everyone who uses email.
Security professionals have been saying it for years. The specific dangers associated with email have changed during that time, but the advice remains valid, and applies to everyone who uses email.
While styled text in emails looks nice, and can increase readability, those benefits are massively outweighed by the associated risks.
I’ve been viewing all incoming email as plain text since I worked at the help desk of a major Canadian university. I saw first hand the damage that could be done with malicious email.
This morning, I received a phishing email that once again reinforced this old, but solid advice.
The Phish
Here’s what the email looks like when viewed in HTML mode, which renders underlying code as styled, formatted text:
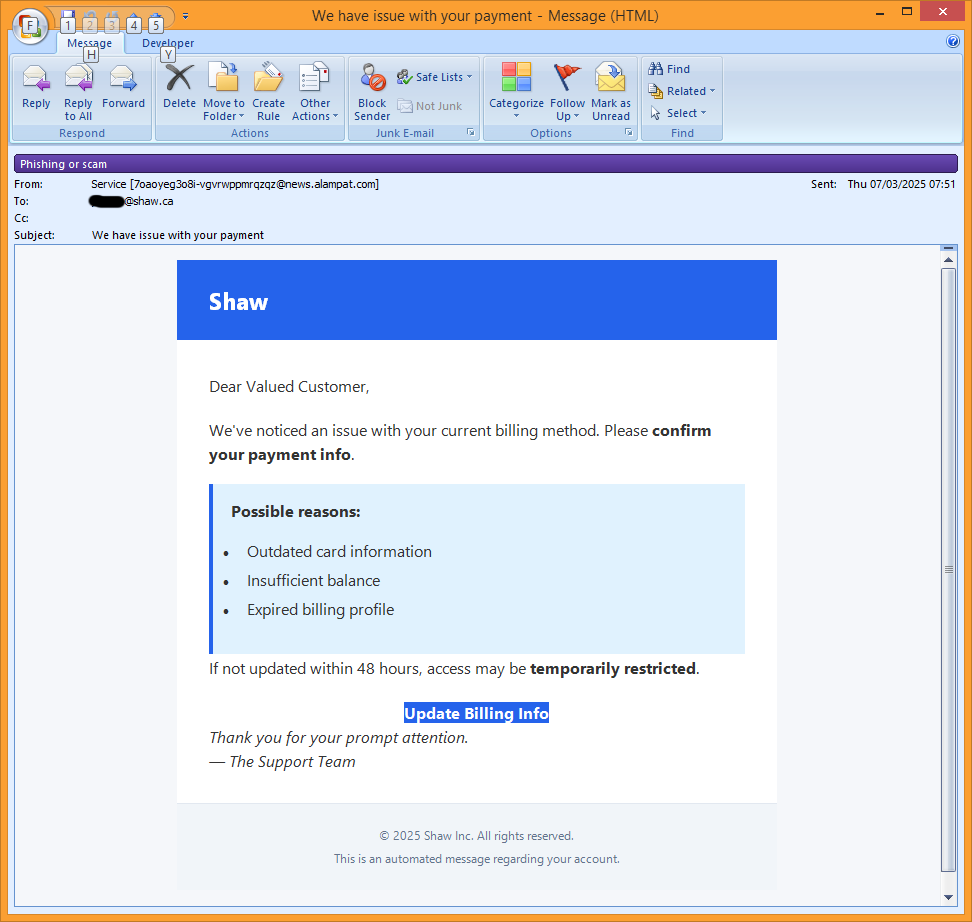
Looks legitimate, at first glance. Upon closer inspection, the ‘From’ address is clearly unrelated to the supposed sender. It’s a long, randomly-generated string of characters, followed by ‘@news.alampat.com’. The long string of random characters may be designed to push the sender’s domain (news.alampat.com) off the screen on some devices. The domain itself doesn’t even exist.
Other than that, nothing suspicious stands out.
Savvy email users also know that you can usually hover the mouse pointer over a button or link, to show the web address hidden behind it. Doing that for this email reveals that clicking the ‘Update Billing Info’ button will send your web browser to: randomtext.valenciaacademy.com.br/randomtext?randomtext-randomtext==
Analysis of the actual address using the amazingly useful site scanner at urlscan.io shows a fake Shaw webmail login page, which looks identical to the actual Shaw webmail login page.
If you clicked the button in the phishing email, you would arrive at this legitimate-looking login screen. If you then entered your Shaw email username and password, the phish would be successful: the perpetrators would have the login ID and password for your email account. Your account could then be used for anything, up to and including identity theft.
Now, here’s what I saw when I opened the same email, which again, I see as plain text because I’ve configured Outlook that way:
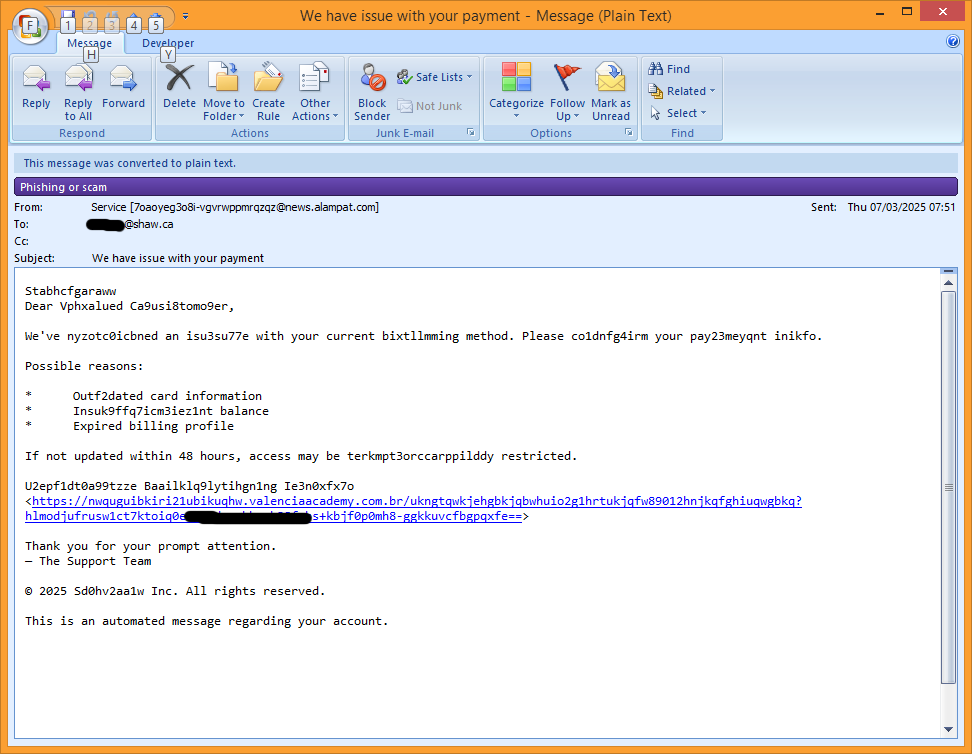
It’s immediately obvious that many important words in the email have been partially obfuscated by inserting garbage characters. These characters are hidden in the HTML view. The web address associated with the ‘Update Billing Info’ button is also shown clearly. And that’s the problem, or rather one of the problems, with viewing email in rendered HTML mode: information is hidden from your view.
If you don’t mind the idea that the email you open includes hidden — and potentially very dangerous — information, I guess you can keep running that risk. But I cannot recommend it.
Take a few minutes to look at your email application’s settings. It should have an option to display all email as plain text. Enable that to improve your email safety.
 boot13
boot13 Yesterday I fired up my media PC, booting to Windows 10, to watch some episodic visual media (you know, TV shows) that we refer to as ‘comfort food’ around here.
Yesterday I fired up my media PC, booting to Windows 10, to watch some episodic visual media (you know, TV shows) that we refer to as ‘comfort food’ around here. The folks at Microsoft are once again demonstrating their creativity in thinking up ways to trick people into using its web search service, Bing.
The folks at Microsoft are once again demonstrating their creativity in thinking up ways to trick people into using its web search service, Bing.
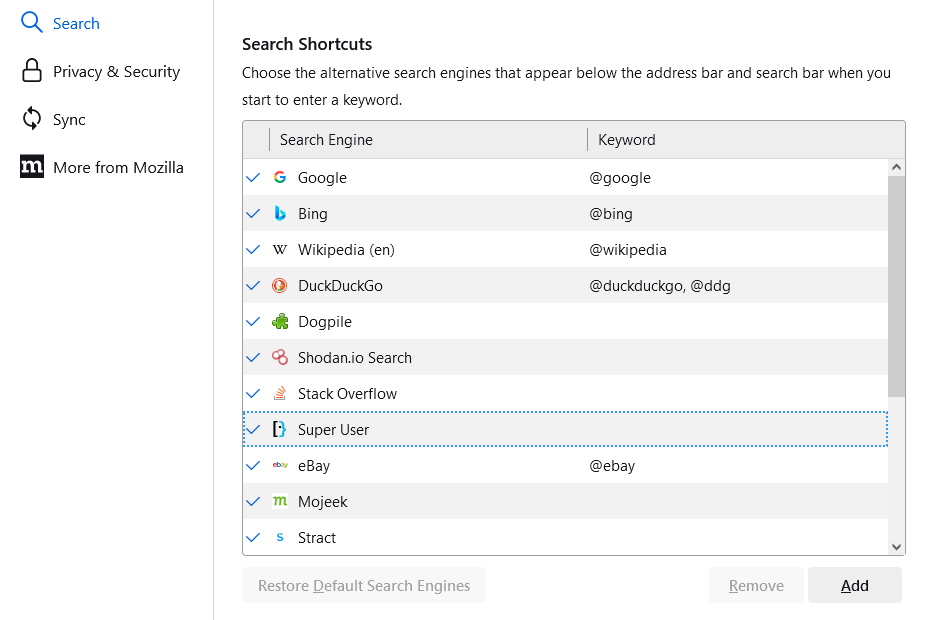
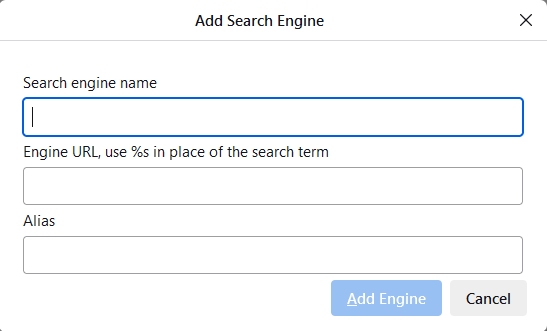 In the small dialog that appears, enter a name for the new search (I call it ‘Google Classic’), the URL
In the small dialog that appears, enter a name for the new search (I call it ‘Google Classic’), the URL 
 If you installed and activated the popular
If you installed and activated the popular  There’s apparently a team of people at Microsoft who spend all their time trying to come up with sneaky ways to get Windows users to switch to Edge as their default web browser. To be clear, I have no direct evidence that such a team exists, but it seems likely.
There’s apparently a team of people at Microsoft who spend all their time trying to come up with sneaky ways to get Windows users to switch to Edge as their default web browser. To be clear, I have no direct evidence that such a team exists, but it seems likely.