 I’ve enjoyed playing around with generative AI tools like ChatGPT and the new, generative features of image editors. I used ChatGPT to generate most of the definitions on this site (which I carefully reviewed and approved before posting). I even tried a code generator, though the code proved unusable.
I’ve enjoyed playing around with generative AI tools like ChatGPT and the new, generative features of image editors. I used ChatGPT to generate most of the definitions on this site (which I carefully reviewed and approved before posting). I even tried a code generator, though the code proved unusable.
But there’s a problem with all these technologies: they’re expensive. It takes a lot of processing power to run these tools. You don’t notice this, because when you ask MS Paint to generate an image, your computer’s fans don’t even speed up. That’s because the real work is always done on a remote computer, or multiple computers, owned by an AI company or some other large company that’s bought into the current AI craze.
Okay, so what? As long as I don’t have to pay for it, why should I care how much processing power is required? First of all, the companies that are are paying for all that work are currently subsidizing it; they are betting enormous amounts of money that these tools are here to stay. Some of them are charging users for their services, but so far none of them are making anywhere near what they’re spending. That’s not sustainable, and eventually they will need to either start recovering their costs, or discontinue their services.
We are starting to see advertising in generative AI services, and while that may offset the costs of running an AI data center to some degree, I doubt ads will come close to paying for all of that infrastructure and energy.
The second problem is that the processing power required by generative AI uses a lot of energy. Like, huge amounts of energy. You don’t see that, but it’s one reason generative AI services are so expensive to operate. Big companies are building huge new data centers just to host generative AI services. And they’re using incredibly large amounts of energy to power them. That’s not going to change, and at some point, government and industry regulators are going to start making noise about it. When an industry uses a lot of energy, regulators uses various methods to curb the excess, including taxes. I predict that governments will start taxing AI companies, which will make generative AI even more expensive.
So again, at some point, companies providing generative AI services will have to recover their ever-increasing costs. There are a few ways to do that, but the most obvious one is to start charging for those services, or to start charging a lot more. That will kill demand for those services, and eventually only organizations with very deep pockets will be able to afford them. At that point, the generative AI bubble will burst, and will fade into the background, just another tech fad that amused us for a while.
The other major issue with generative AI is legality. All generative AI uses existing media, much of which is obtained from public sources. The legal fights about this have only just started, and will only get worse as service providers start trying to make money from what is basically the work of other people. It will be interesting to watch as an outsider, and will keep copyright lawyers working for years.
NVIDIA
NVIDIA manufactures the processing chips that power generative AI. At this point I think the smart move would be to start short-selling NVIDIA stock, the value of which is currently skyrocketing, based on an assumption that generative AI is here to stay. When the NVIDIA stock tanks after this AI craze, anyone brave enough to short it will make enormous amounts of money.
Conclusions
Of course, it’s always possible that there will be a breakthrough in processing power, or the associated power requirements, and if that happens soon enough, my predictions could end up being way off. But it would need to be a big breakthrough, and that doesn’t seem likely.
So, enjoy these interesting AI tools while they last. Just don’t count on being able to afford using them in a few years. If you’re a writer, artist, or programmer who depends on generative AI tools for your livelihood, you are heading for trouble.
UPDATE 2026Mar06: here’s a fascinating ‘interview’ with the Claude chatbot, in which the human interviewer asks a series of questions about the financial realities of Nvidia’s stock price, and the viability of AI-powered services. Claude is not optimistic.
 boot13
boot13 Security professionals have been saying it for years. The specific dangers associated with email have changed during that time, but the advice remains valid, and applies to everyone who uses email.
Security professionals have been saying it for years. The specific dangers associated with email have changed during that time, but the advice remains valid, and applies to everyone who uses email.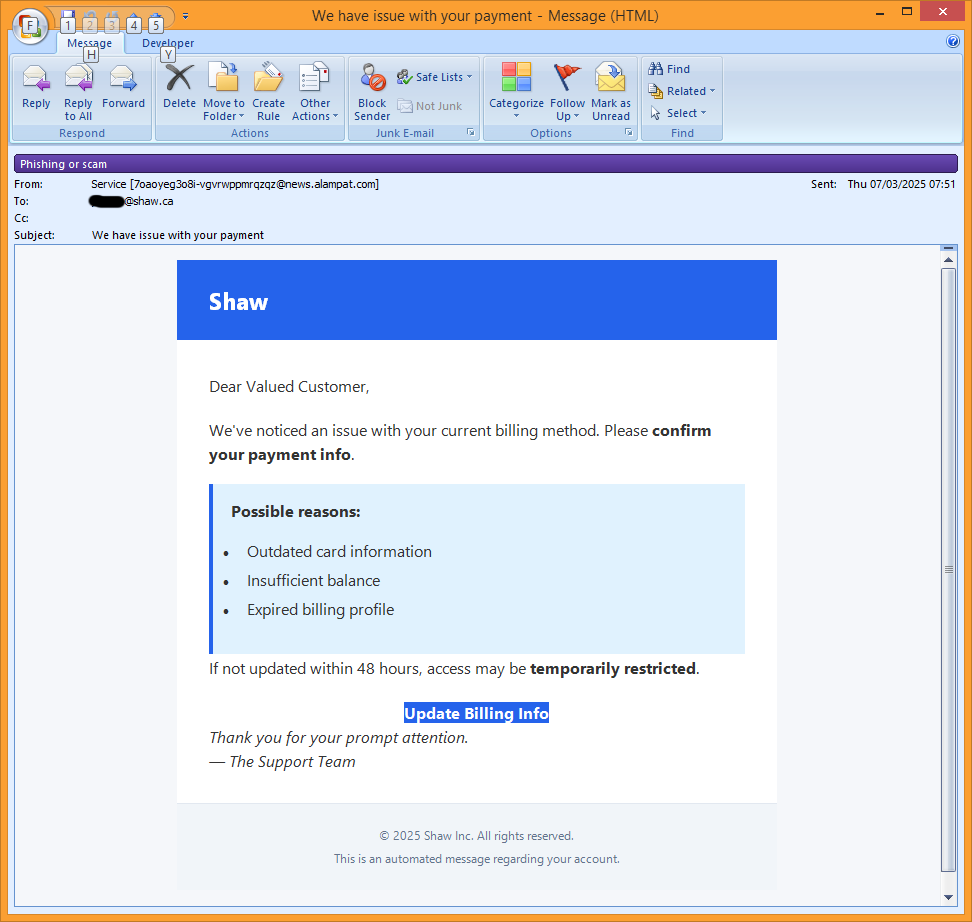
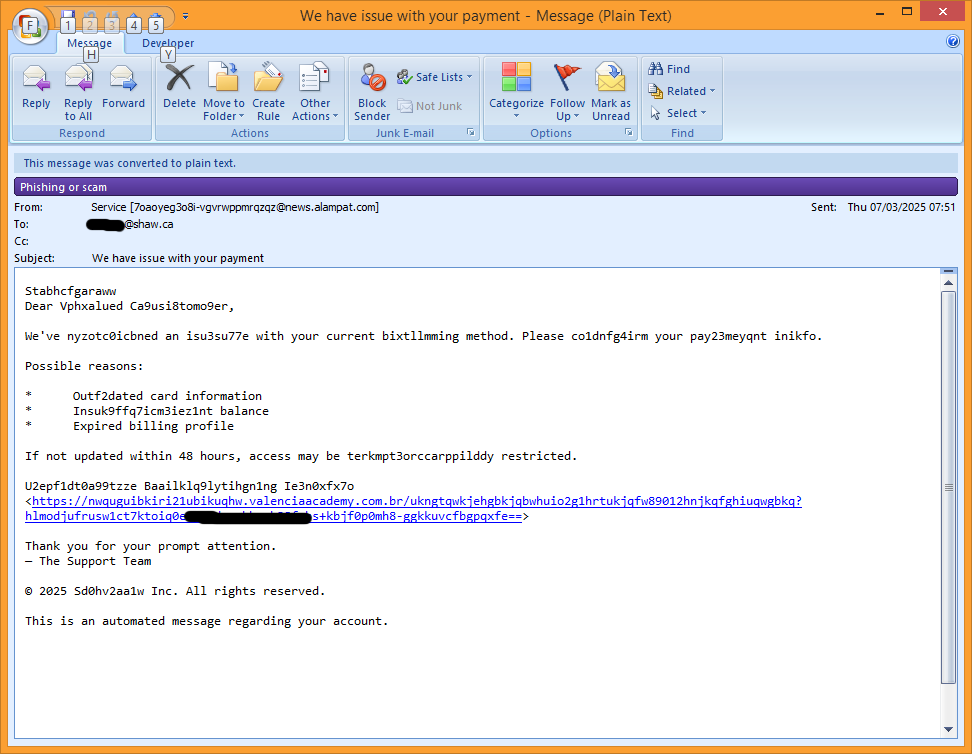
 Yesterday I fired up my media PC, booting to Windows 10, to watch some episodic visual media (you know, TV shows) that we refer to as ‘comfort food’ around here.
Yesterday I fired up my media PC, booting to Windows 10, to watch some episodic visual media (you know, TV shows) that we refer to as ‘comfort food’ around here. The folks at Microsoft are once again demonstrating their creativity in thinking up ways to trick people into using its web search service, Bing.
The folks at Microsoft are once again demonstrating their creativity in thinking up ways to trick people into using its web search service, Bing.
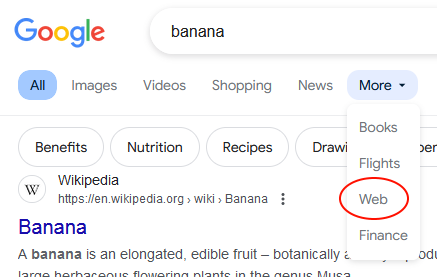
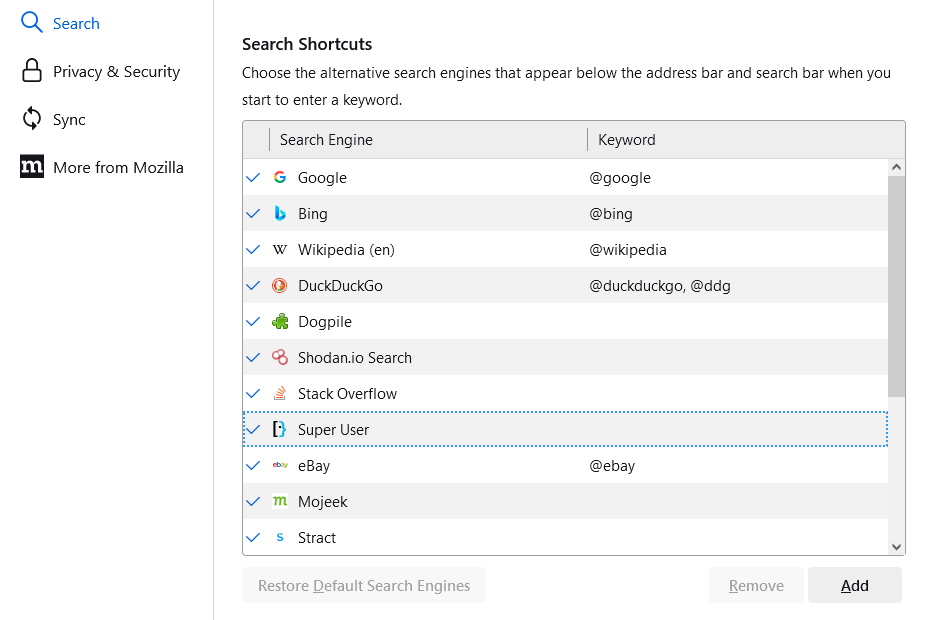
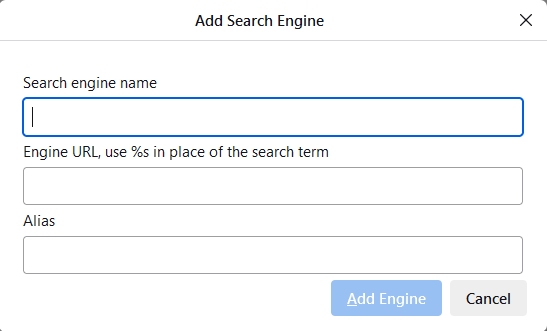 In the small dialog that appears, enter a name for the new search (I call it ‘Google Classic’), the URL
In the small dialog that appears, enter a name for the new search (I call it ‘Google Classic’), the URL 
 If you installed and activated the popular
If you installed and activated the popular  There’s apparently a team of people at Microsoft who spend all their time trying to come up with sneaky ways to get Windows users to switch to Edge as their default web browser. To be clear, I have no direct evidence that such a team exists, but it seems likely.
There’s apparently a team of people at Microsoft who spend all their time trying to come up with sneaky ways to get Windows users to switch to Edge as their default web browser. To be clear, I have no direct evidence that such a team exists, but it seems likely.