Authorities from several countries have successfully neutralized the relatively small, but technically sophisticated botnet Beebone. At least 12,000 computers are still infected with the malware, but it has been rendered toothless through a process known as sinkholing.
Category Archives: Internet crime
WordPress sites targeted by pro-ISIL hacks
An active campaign pushing the agenda of ISIL is being perpetrated mainly via hacked WordPress sites. The FBI has issued a related warning.
Anyone who runs a WordPress site should immediately ensure that it is up to date with all WordPress and plugin updates. Of course this won’t help if your site has already been hacked, so if you have any doubt, please scan your site with one (or preferably all) of the following web-based site scanners:
Meanwhile, yet another popular WordPress plugin has been found to contain a serious vulnerability. The site caching plugin WP-Super-Cache has a nasty cross-site scripting bug. Anyone using this plugin on a WordPress site needs to update it to the fixed version (1.4.4) immediately.
Malvertising is a growing threat
If you’re not familiar with the term, you should be. ‘Malvertising‘ refers to the increasingly common tactic whereby malicious persons include exploit code within what otherwise appears to be legitimate, web-based advertising.
Over on eWEEK, a recent post (Why ‘Malvertising’ Has Become a Pervasive Security Risk) explains why Malvertising is a real and growing threat.
Organizations that provide advertising platforms – including Google – need to deal with this threat quickly. If they don’t, there’s likely to be a surge in users installing ad-blocking software in their browsers. I personally use and recommend NoScript, a browser plugin that blocks all Javascript (and Malvertising) by default.
Ramnit botnet suppressed
Europol, with assistance from Microsoft, Symantec, and Anubis Networks, has identified and seized the servers thought to be at the core of Ramnit‘s infrastructure.
Ramnit began operations in 2010, and has evolved from a simple worm to include advanced features for stealing personal/banking information and self-propagation. In its latest incarnation, Ramnit is capable of compromising infected computers in numerous ways. In 2012, Ramnit was used to gain access to 45,000 Facebook accounts.
Only time will tell whether this crackdown has actually succeeded in ridding the world of this particular piece of malware.
Reporting hack attempts, phishing and spam
Over the years, I’ve tried to be a good Internet citizen and report abuse (hack attempts, spam, etc.) This can be a daunting task, and the results are often less than satisfactory. For most people, the time wasted on spotting and deleting spam is bad enough; the extra work of reporting spam can seem like a tedious chore.
Reporting abuse can produce wildly varying results. Here are a few examples from my own recent experience:
BT Italy
Over the past couple of months, one of the WordPress sites I manage has seen a steady stream of ‘admin’ login attempts from computers in Italy, most of which connect to the Internet via the ISPs albacom.net and fastweb.it. Literally thousands of different albacom.net and fastweb.it IP addresses were being used in the attacks.
Since the majority of these login attempts were from albacom.net, I initially focused on Albacom. I discovered that most of the devices at the other end of these attacks were Aethra BG1242W ISDN modem/routers. These appear to be the standard modem/router provided by Albacom to their customers. I was horrified to find that I could log into these devices via their web interface. Clearly Albacom’s dedication to security is severely lacking. Of course it’s difficult to know for sure whether the attacks were coming directly from these (presumably hacked) routers, or from (also presumably hacked) computers connected to them.
Apparently, British Telecom (BT Italy) is in the process of acquiring Albacom. This is undoubtedly creating some confusion there, but that’s really no excuse for any of this.
I tried various methods for reporting this to Albacom:
- sent email to the abuse address on record for albacom.net, but every attempt bounced, saying that the user’s mailbox was full;
- sent email to the technical contact on record for albacom.net, but this was ignored;
- tweeted about the problem on the main BT Twitter account, but my tweets were immediately deleted.
This is a terrific example of how not to handle abuse reports. I don’t know what’s going on with BT ITaly, but clearly they are having serious issues.
I also reported this on the Wordfence support forum, to see if anyone else might be seeing this problem. Wordfence is an excellent WordPress security plugin, and it was Wordfence that was detecting (and blocking) these login attempts. Sure enough, several other people reported seeing this problem on their sites.
A few weeks later, the login attempts from Italy stopped – for my own site and for others. Then they started up again for some sites, but luckily not for mine.
SpamCop
I recently signed up at SpamCop.net and started submitting the numerous spam messages I receive daily for one particular address. SpamCop’s submission process analyzes submitted email and makes recommendations about where to report it. Note: you must configure your email client so that you can see the entire message source, including all headers, for this to work.
The submission process is well explained at each stage, and provides useful warnings to the submitter about making sure that the submission is actually spam, and so on. A lot of technical information is displayed with the analysis, but much of that can be hidden if you prefer to concentrate on the basics.
SpamCop uses spam submissions to create a block list, which is used in conjunction with similar lists from other sources, by ISPs and other mail providers, to help filter out spam before it reaches user inboxes.
If you’re willing to put in the effort, I highly recommend signing up.
Moonfruit
A few days ago, I received this (admittedly very lame) phishing attempt in my inbox:
Your mailbox is full of, 00.1 GB, Please reduce your mailbox size.
Delete any items you don't need from your mailbox and expand your
email quota (size) with the below web links: CLICK HERE
http://REMOVED.moonfruit.com/
Thank you for your understanding.
©2015 Helpdesk
I went to the site in question (with NoScript enabled and blocking all scripts) and confirmed that this was indeed an attempt to con me into entering private information into a form.
A bit of searching revealed that Moonfruit is a web-based service that allows clients to set up web sites with minimal effort. It’s a totally legitimate company. Customer web sites hosted by Moonfruit have URLs like this: whatever.moonfruit.com. Whoever set up the phishing site just happened to use Moonfruit as the host.
So I decided to try reporting this to Moonfruit support. I easily found the contact page on their web site and submitted a general query about the phishing attempt, including the text of the email. I wasn’t sure this would amount to anything, especially since I’m not a Moonfruit customer. I immediately received a confirmation of my submission, and was then delighted to receive the following response from Moonfruit, within an hour of my submission:
Thanks for bringing this to our attention.
We have closed the site and the associated accounts, and banned the user.
Now THAT’S how you deal with abuse reports. Nice work, Moonfruit!
Tax-related scam emails appearing
I just received email purporting to be from Revenue Canada, telling me that I have overpaid my taxes in recent years, and urging me to claim my refund by clicking on a link.
The link actually goes to a Cloudflare-hosted web site, epathchina(.com). The site has nothing to do with Revenue Canada, and exists to trick unsuspecting people into divulging private/financial information to the site’s operators.
Currently, the site shows nothing untoward in Sucuri site check: it’s not on any blacklists and malware scans show nothing. But that’s likely to change.
With tax time nearing, we should expect email like this to appear in our inboxes. As a general rule, it’s a bad idea to click links in email. Of course, if you’re certain the source is legitimate, the risk is far less, but it’s still possible that the ‘legitimate’ source has been compromised. In this particular case, a much safer approach is to simply go to the Canada Revenue web site and log in.
Clues that this was a scam email:
- The Return-Path address (refund AT server.whitetails.com) is unrelated to Revenue Canada.
- The From address is to a domain that appears to be related to Revenue Canada (craarc.gc.ca), but doesn’t actually exist, as confirmed by any IP checking service like WhatMyIP.
- Like most effective cons, it offers money for nothing.
- The recipient is urged to act quickly.
- The message is poorly formatted.
- The recipient is instructed not to contact Revenue Canada by telephone.
Recommendations: configure your email client to display email in plain text format and display all headers. This will make your inbox less entertaining, but a lot safer, since it will much easier to spot suspicious links and headers.
Here’s the body of the email:
Dear Applicant:
Following an upgrade of our computer systems and review of our records we
have investigated your payments and latest tax returns over the last seven
years our calculations show you have made over payments of 226.99 CADDue to the high volume of refunds due you must complete the on line application,
the telephone help line is unable to assist with this application.To access the form for your tax refund,please click here
Your refund may take up to 3 weeks to process please make sure you complete the form correctly.
As we are upgrading our records we require the completed form showing your full current details by 10 February 2015
Please complete the form to confirm the refund.
A. B. Marions
Senior Manager
Canada Revenue Agency————————————————————–
© Copyright 2015, Canada Revenue Agency All rights reserved.
TAX REFUND ID: XXXXXXXXXXXXX
Brian Krebs recently reported on another tax-related scam affecting Americans, in which stolen credentials are used to post fraudulent tax returns.
CryptoWall update
Despite the demise of CryptoLocker, ransomware is still prevalent, mostly in the form of CryptoWall, now in its ‘improved’ 2.0 version.
Security researchers recently deconstructed CryptoWall 2.0 and shared their findings in a post on a Cisco security blog.
The researchers discovered that the malware uses a variety of techniques to obfuscate itself on target systems. It’s also able to infect both 32 and 64 bit Windows systems. And it can detect whether it’s running on a virtual machine, making it more difficult to analyze. The command and control servers are apparently in Russia.
A Windows computer can become infected with CryptoWall in a variety of ways, including as part of an e-mail ‘phishing’ attack, through a malicious website, via malicious PDF files, or in a spam e-mail disguised as an ‘Incoming Fax Report’.
Ars Technica has additional details.
DDoS services powered by compromised routers
Malicious hackers are increasingly using compromised, consumer-grade routers to amplify the power of their DDoS attacks. Ordinary users are often unaware that their network devices can be compromised, and even less likely to recognize any actual compromise.
Adding to the problem is the slow pace – or utter lack – of security updates from device manufacturers. Even when updates are made available, users are unlikely to know about them, and in most cases don’t possess the skill required to install them.
All of this makes routers attractive targets. Ars Technica reports on one DDoS-for-hire service that uses a vast network of compromised routers.
There’s a related post on Brian Krebs’ blog. Scroll down to ‘ROUTER SECURITY 101’ for some useful recommendations. At the very least, log in to your router’s admin interface and check for any available security updates.
Millions of network routers vulnerable to hijacking
As many as twelve million routers in use in homes and businesses around the world contain a bug that makes them vulnerable to a particular form of attack. Routers made by Linksys, D-Link, Edimax, Huawei, TP-Link, ZTE, ZyXEL and others are affected (see this list of affected routers – warning: PDF).
The vulnerability exists in a particular piece of software called RomPager. This software is embedded in the firmware of the affected routers.
Routers typically provide a mechanism for updating their firmware, but router manufacturers are often slow to provide updates, and the update process can be problematic, especially for regular users.
As a result, this problem is likely to hang around for years, and will not be completely eliminated until all of the affected routers are updated or replaced.
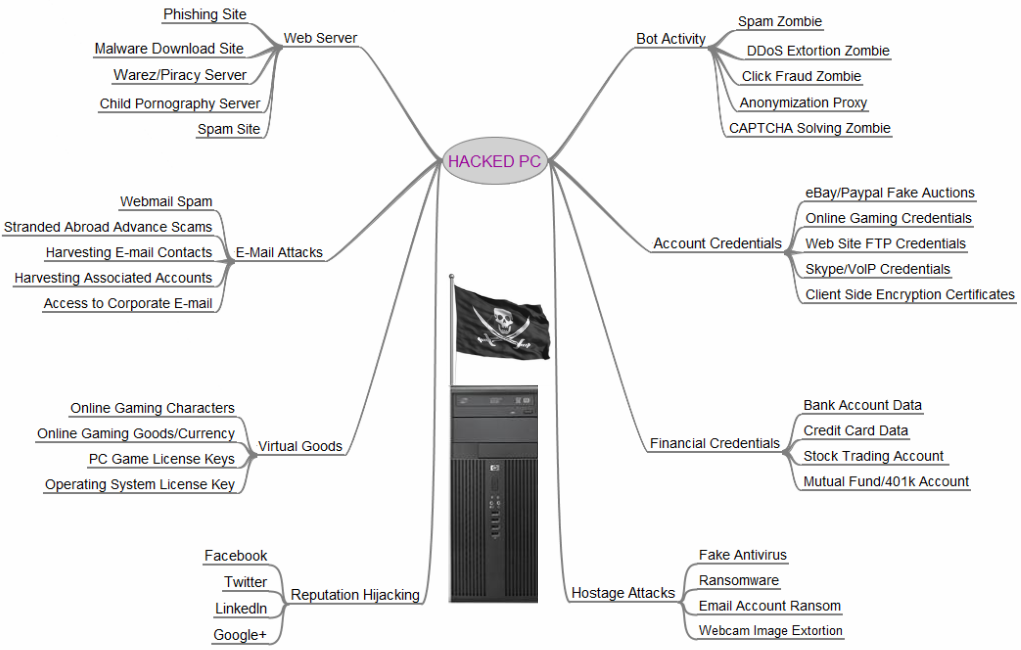
Even the crappiest computer is worth hacking
If you’re like a lot of other typical users, you may believe that nothing on your computer makes it a worthwhile target for malicious hackers. You may even feel that this means you’re relatively safe from hackers. Think again.
To a malicious hacker, the Internet is a vast, mostly untapped ocean of computing resources, ready for them to compromise and put to work in numerous ways to help them and hurt you.
Brian Krebs created and posted the image below to remind people of all the ways their computers can be secretly used for nefarious purposes. Although the post is a couple of years old, it’s still relevant.
 boot13
boot13