The free-for-personal-use remote control software TeamViewer is currently under intense scrutiny. Large numbers of users are reporting unauthorized access to their computers, theft of login credentials, and in some cases, access to online financial systems and theft of funds.
It remains unclear exactly how these unauthorized intrusions are happening. TeamViewer officials are so far denying that the software has been hacked, insisting that the current surge in TeamViewer-based attacks are the result of password re-use, combined with the recent publication of several databases of stolen credentials.
Until we know for sure what’s going on, we recommend removing TeamViewer from all computers on which it is installed.
If removal is not an option, as may the case for some support setups, then you should configure TeamViewer to not start with Windows, only start it when asked to do so by support staff, and then close it when their work is complete.
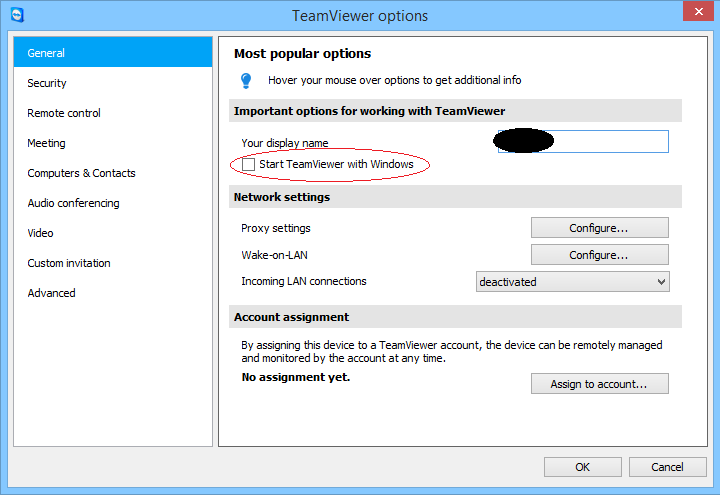
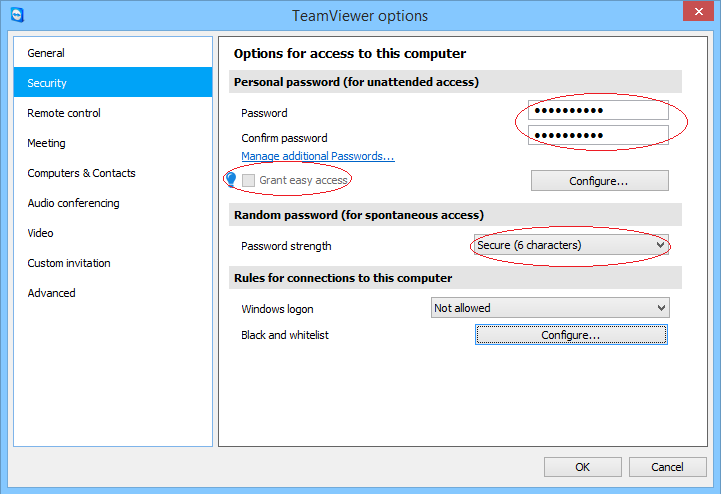
You should also avoid using fixed, personal passwords, relying instead on the temporary passwords TeamViewer generates when it is started, or at least make sure that your personal passwords are strong and unique. Oddly, there’s no way to disable a fixed, personal password, once it’s set up, so your only option in that case is to set it to something very long and random.
Criticism of TeamViewer is building, and the company’s response to this issue has been somewhat less than stellar. If they are convinced that the problem is re-used passwords, why have they not forced a password change for all TeamViewer accounts?
TeamViewer’s makers also seem unwilling to consider the notion that the software itself has been hacked in some way, instead focusing on TeamViewer accounts. An account is not required to use TeamViewer, and exists only as a master address book for people who use TeamViewer to access many different computers. If your TeamViewer account is compromised, an attacker will then have full access to all computers in your account.
To their credit, Teamviewer is working to add new features to the software that should beef up its security. But the new features only affect TeamViewer accounts. If you don’t have a TeamViewer account, you won’t see any benefit.
Update 2016Jun06: TeamViewer management continues to insist that the problem only affects TeamViewer accounts, not the TV desktop client. We recommend avoiding TV accounts if possible. If that’s not an option, make sure you enable two factor authentication (2FA) for the account, and use a complex, unique password.
There’s a lot of discussion about this over on Reddit. One post contains reports from users who have experienced TeamViewer-related intrusions. Another provides instructions for determining whether your computer has been accessed via unauthorized use of TeamViewer.
Meanwhile, we’re wondering whether it might be helpful if TeamViewer showed a large red warning when setting up an account, like this:
WARNING: if there's only one site or service where you use a strong password, let it be your TeamViewer account. Because if someone gets access to your TeamViewer account, they will also have full access to all of the computers you access through your account.
 boot13
boot13