 Backups are important. I tell people that they should think about how much work would be involved if they lost all their data, and had to create or gather it all again. Considering that work is usually enough to get people talking seriously about backups.
Backups are important. I tell people that they should think about how much work would be involved if they lost all their data, and had to create or gather it all again. Considering that work is usually enough to get people talking seriously about backups.
This consideration informs decisions about the backup process to be used: what should be backed up, how often backups should run, where backups will be stored, and how many backup versions will be kept.
My own backup requirements are like those of anyone who has done any amount of work that they would hate to lose: documents, email, financial records, pictures, artwork, and even browser bookmarks. The only difference is that I also provide full or partial backup services to my clients.
A few years ago, I realized that I needed an off-site backup system to complement my local backups. In the nightmare scenario involving total loss of all computers and storage devices resulting from a house or office fire, all local backups would also be lost.
And so I started looking at backup software that would allow me to maintain backups of critical data somewhere besides my home/office.
Storage required
Off-site backup storage takes many forms, including taking physical backup media off-site daily. These days it most often involves a paid service such as Amazon S3.
Remote services are often referred to as ‘cloud’ services, but they mean the same thing: the service runs on someone else’s computer. Of course, storing your irreplacable, private data on someone else’s computer sounds scarier than storing it ‘in the cloud’ so that’s the term we hear most often.
There are some special considerations when you start looking at using cloud storage for backups: additional costs, network bandwidth, vendor trustworthiness, privacy, and encryption.
The encryption issue alone requires careful consideration. Is your data encrypted in transit? Is it stored in encrypted form on the cloud service? Who has the keys to decrypt your data?
For my own backups, I settled on the DreamObjects storage service provided by Dreamhost. I’ve been using Dreamhost for client web sites and related services for years, and I’ve always found their support to be first rate. I have had a few problems with the DreamObjects service, including some reliability issues, but these were resolved quickly and satisfactorily by Dreamhost support.
My requirements
In my recent search for an off-site backup solution, I settled on the following requirements:
- Runs on my main PC (Windows 8.1).
- Stable and reliable.
- Reasonably fast.
- Incremental backups (back up only changed files).
- Transmit only changed data (to save bandwidth).
- A built-in scheduler, or compatibility with Windows Task Scheduler.
- Compatible with DreamObjects, itself an S3-compatible service.
- Data is encrypted in transit and when stored.
- Storage provider does not possess encryption keys.
- Ability to limit bandwidth used during backup operations.
- Ability to limit the amount of storage used.
- Backup storage pruning based on number of copies and/or storage used.
- Straightforward restore process and tools.
- Useful logging.
- Does not use excessive computing resources (memory, processor, local storage, handles, and disk I/O).
- The ability to include and exclude files and folders based on various criteria.
Enter CloudBerry
I looked at numerous possible solutions, and even purchased a few that looked promising but ultimately failed to meet my requirements, including qBackup, Arq5, Arq7, and GoodSync. I also looked again at Cobian Backup, which I still use for local backups, and Allway Sync, which I use for fast syncing of critical data to thumb drives, but they also failed to meet my needs for off-site backup.
CloudBerry was just the next solution on my list. I had never even heard of it before reading about it in this Reddit thread.
CloudBerry Backup can be downloaded and installed on a trial basis for two weeks. That was plenty long enough for me to learn what I needed.
CloudBerry Backup Features
See that list of requirements a few paragraphs back? Well, CloudBerry Backup checks all those boxes, and then some. CBB works with many storage services, including Amazon S3, Amazon S3 Glacier, Microsoft Azure, Google Cloud, Backblaze B2, Wasabi, OpenStack, various S3-compatible storage and others.
Other notable CloudBerry Backup features:
- Grandfather-Father-Son (GFS) retention policy support
- Backups to local drives and NAS-like storage devices
- Microsoft SQL Server backups
- Microsoft Exchange backups
- Synthetic Backup for File, Image-based, VMware backups
- Bare-metal recovery (create recovery disks and USB drives)
- Cloud Backups (cloud-to-cloud, and cloud-to-local)
- Image-based backups (physical or virtual machine image)
- Modified Block Tracking for Image-based backups
- Support for various virtual machine formats (Hyper-V, VMware, VirtualBox, and RAW)
- Restoring image-based backups as Amazon EC2, Microsoft Azure VM, and Google Compute Engine instances
- Hybrid (two-step) backup (applies to the legacy format only)
- Client-side Deduplication
- Mandatory and Full Consistency Checks
- Backup Chains and Custom Scripts Support
One huge bonus CloudBerry provides is a clean, well thought-out user interface. This wasn’t on my requirements list, because although UI is important, backup software is typically set up once and then runs in the background. So I can live with a crappy UI in backup software, as long as it’s otherwise good. That’s unlike software I use every day, such as my email client, web browser, and document-based office applications.
A well thought-out user interface also makes CloudBerry Backup a legitimate solution for the less technically-inclined among us. In using CBB, I frequently discovered what I was looking for without any searching for functions or settings. Preset defaults made sense, and the backup plan creation wizard is excellent. CBB even creates several backup plans automatically, for documents, web browser bookmarks, and pictures; these need only a destination to be configured before they can be used.
CloudBerry Backup Pricing and Licensing
CloudBerry Lab was founded in 2011, but is in the process of rebranding itself as MSP360, so the company web site refers to both names. For now, the product I’m interested in is MSP360’s CloudBerry Backup Desktop Edition, which sells for $49.99 USD. The company provides other backup software and services aimed at business, corporate, and educational customers. There’s also a free version of CloudBerry Backup, but it has some limitations that make it unsuitable for my purposes.
When you purchase CloudBerry Backup Desktop Edition, you have the option of paying an extra $10 USD for a year of annual maintenance. The MSP360 web site isn’t exactly clear about what this provides, but it does include support, and may be the only way to obtain software updates. If you want and/or need support, the $10/year price seems reasonable.
Conclusions
Great software makes me happy. CloudBerry Backup qualifies, and my search for an off-site backup solution is over for now.
If you or anyone you know could use an excellent backup solution, whether or not they need off-site storage, you won’t go wrong recommending CloudBerry Backup.

 boot13
boot13 As I’m sure you’ve noticed by now, I’m using
As I’m sure you’ve noticed by now, I’m using  Using a password manager is still the best way to securely record all your passwords. This assumes that you are in fact using different passwords for every web site and service that require one. If you’re using the same password for everything, you are risking your privacy, financial security, and sanity.
Using a password manager is still the best way to securely record all your passwords. This assumes that you are in fact using different passwords for every web site and service that require one. If you’re using the same password for everything, you are risking your privacy, financial security, and sanity.
 In brief: stay away from this software.
In brief: stay away from this software.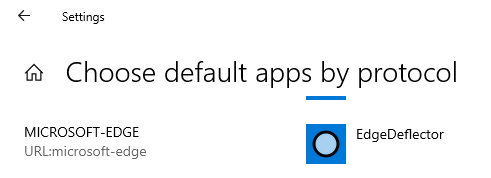
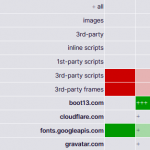 I just discovered an interesting and useful web site:
I just discovered an interesting and useful web site:  A new software tool from
A new software tool from