You may have noticed that Google Search results are getting crappier. The ads are still fairly unobtrusive, but a typical search results page is filled with other junk that is often of no interest at all.
The good news is that Google just enabled a new feature in Search that may remind you of the good old days when search results were less cluttered. It’s called ‘Web search’. No kidding.
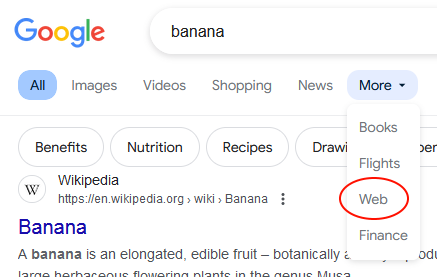
To see Web search in action, go to google.com and search for something. Near the top of the search results page, you should see a horizontal menu, starting with ‘All’, ‘Images’, and ‘Videos’. Click the ‘More’ entry, and select ‘Web’.
As you can see, this cleans up the results page significantly.
I like this feature so much that I’ve made it my default search in Firefox. Here’s how to do that:
- By default, you can’t add custom search engines to Firefox. To enable that function, enter
about:configin Firefox’s address bar and press Enter. You’ll be asked if you’re sure you want to proceed; click ‘Accept the risk’. Then typebrowser.urlbar.update2.engineAliasRefresh. You should see a small ‘+’ box to the right. Click that. - Click Firefox’s ‘hamburger’ menu button, which looks like three horizontal lines, at the top right. Select ‘Settings’.
- Click ‘Search’ in the left sidebar.
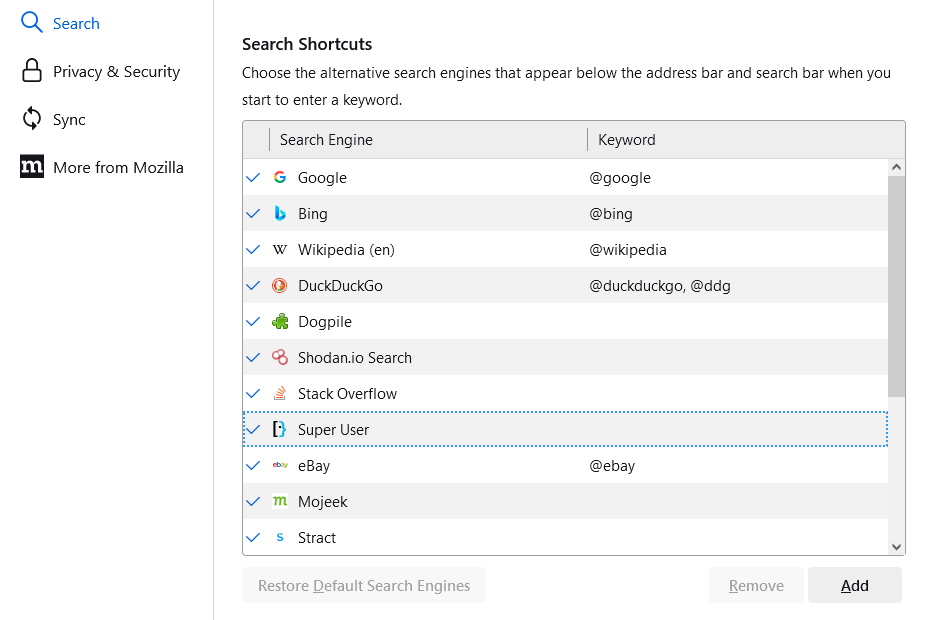
- Scroll down to the ‘Search Shortcuts’ list. At the botton of that list, there should be an ‘Add’ button. Click that.
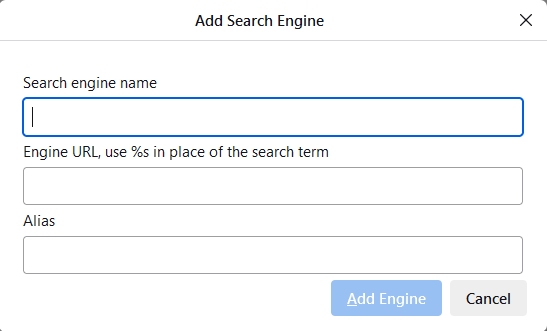 In the small dialog that appears, enter a name for the new search (I call it ‘Google Classic’), the URL
In the small dialog that appears, enter a name for the new search (I call it ‘Google Classic’), the URL https://www.google.com/search?q=%s&udm=14, and then give it a shortcut alias like ‘gc’. Then click ‘Add Engine’.- Scroll up the Settings page until you see ‘Default Search Engine’. Click the drop-down list and select the search engine you just added.
After making these changes, searches you perform in Firefox (by entering search terms in the address bar or search box) should produce ‘Web’ search results.
 boot13
boot13
 It could be argued that Microsoft has done us all a favour in making Windows 10’s updates unavoidable. Certainly, as long as nothing goes wrong, it’s less work than futzing around with Windows Update on every computer. And forced updates mean that Windows computers used by less tech-savvy folks stay up to date with security fixes, which makes everyone safer.
It could be argued that Microsoft has done us all a favour in making Windows 10’s updates unavoidable. Certainly, as long as nothing goes wrong, it’s less work than futzing around with Windows Update on every computer. And forced updates mean that Windows computers used by less tech-savvy folks stay up to date with security fixes, which makes everyone safer. First up, there’s been an
First up, there’s been an  Meanwhile, Google is planning to
Meanwhile, Google is planning to