There’s not much to talk about in Chrome 55.0.2883.87. The change log lists about thirteen actual changes, but none of those are related to security and they’re all relatively minor.
Category Archives: Google
Chrome 55.0.2883.75
A new version of Chrome fixes at least thirty-six security issues in the browser. Aside from listing the vulnerabilities addressed, the release announcement says only that Chrome 55.0.2883.75 “contains a number of fixes and improvements”. You’ll have to read the change log to figure out what else is different. Sadly, the full change log is another one of those browser-killing monstrosities, with almost 10,000 changes listed. Don’t click that link if you have an older computer.
SHA-1 deprecation coming soon
SHA-1 (Secure Hash Algorithm 1) is still used by some web sites to encrypt their traffic. Starting in early 2017, most web browsers will start displaying scary-looking warnings when anyone tries to visit sites using SHA-1.
Like this one in Edge:
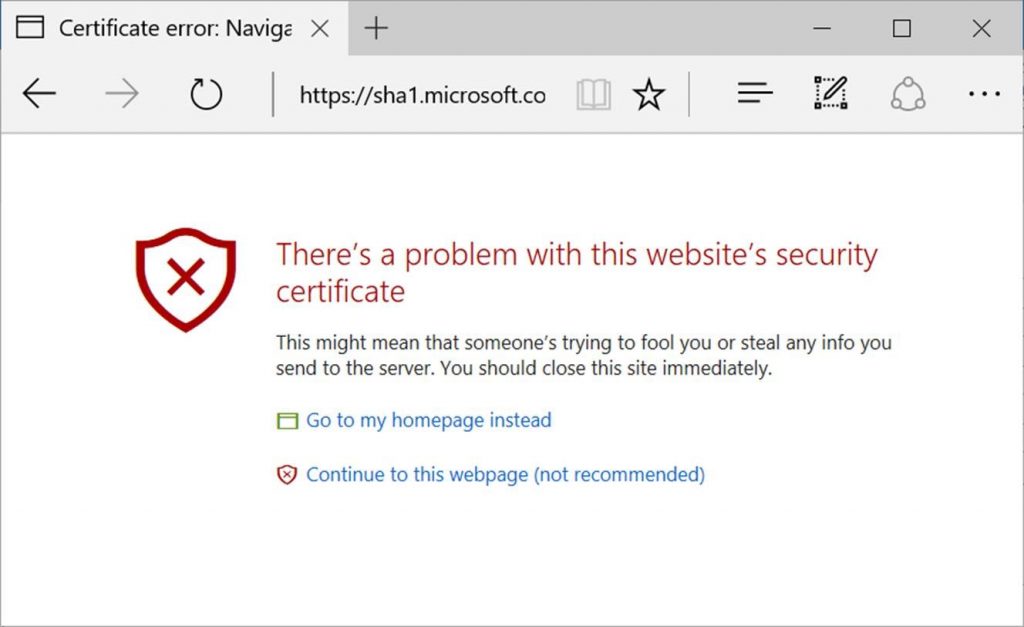
SHA-1 deprecation announcements
Microsoft
(From a post on the Microsoft Edge blog.)
Starting on February 14th, 2017, Microsoft Edge and Internet Explorer 11 will prevent sites that are protected with a SHA-1 certificate from loading and will display an invalid certificate warning. Though we strongly discourage it, users will have the option to ignore the error and continue to the website.
Mozilla
From a post on the Mozilla security blog.
In early 2017, Firefox will show an overridable “Untrusted Connection” error whenever a SHA-1 certificate is encountered that chains up to a root certificate included in Mozilla’s CA Certificate Program. SHA-1 certificates that chain up to a manually-imported root certificate, as specified by the user, will continue to be supported by default; this will continue allowing certain enterprise root use cases, though we strongly encourage everyone to migrate away from SHA-1 as quickly as possible.
From a post on the Google security blog.
We are planning to remove support for SHA-1 certificates in Chrome 56, which will be released to the stable channel around the end of January 2017. The removal will follow the Chrome release process, moving from Dev to Beta to Stable; there won’t be a date-based change in behaviour.
Google gets tougher on scammy web sites
If you use Google search (and really, who doesn’t?), you’ve probably noticed the big warnings that appear when you try to click on some search results. That’s Google Safe Browsing (GSB), protecting you from a malicious web site.
GSB flags sites that fail to comply with Google’s Malware, Unwanted Software, Phishing, and Social Engineering Policies.
To get rid of the warning, the owner of a site flagged by GSB must remove objectionable content and resubmit the site for verification in Google Search Console. Until recently, this process could be repeated indefinitely.
To counter repeat offenders, Google has changed the way GSB works. If a web site repeatedly fails to comply with Google’s Safe Browsing policies, it will be flagged as such, and the warning users see will appear for at least 30 days.
In the announcement for this change, Google points out that the new repeat offender policy will not apply to sites that have been hacked (i.e. changed without the owner’s permission).
Chrome 54.0.2840.99
Chrome 54.0.2840.99 fixes about ten bugs, including four related to security. If you use Chrome, make sure it’s up to date: click the ‘three vertical dots’ menu button at the top right, then click Help > About to check. This will also trigger an update if it hasn’t happened already.
The full change log has additional details.
Windows zero-day vulnerability won’t be fixed until November 8
Google’s Threat Analysis Group recently discovered critical flaws in Flash and Windows that could allow an attacker to bypass Windows security mechanisms. Attacks based on these flaws have already been observed in the wild.
The flaw in Flash was fixed immediately by Oracle; hence the out-of-cycle Flash update on October 26. But Microsoft decided to delay the corresponding Windows fix until next Patch Tuesday (November 8), and is now rather annoyed with Google for reporting the vulnerability publicly. Google was following its own rules for vulnerability disclosure, but such rules differ widely between organizations. In any case, Microsoft would have been happier if Google had waited a bit longer before spilling the beans.
Chrome 54.0.2840.87
According to Google’s announcement, Chrome 54.0.2840.87 fixes at least one security issue. The change log lists forty-seven changes, none of which look particularly interesting or important. Still, this is a security fix, so you should make sure that Chrome has updated itself – if you use it.
Chrome 54.0.2840.71
The full change log lists forty changes in Chrome 54.0.2840.71. None of them seem to be related to security, but at least one is a fix for a crashing issue. The release announcement doesn’t get into any specifics.
Chrome 54.0.2840.59
A new version of Google’s Chrome web browser includes fixes for at least twenty-one security issues.
According to the announcement, Chrome 54 “contains a number of fixes and improvements”, but it doesn’t mention any specifics. If you want to know exactly what’s different, you’ll have to risk crashing your web browser and look at the full change log, which lists at least 10,000 changes.
For most users, Chrome will update itself over the next few days. You can usually trigger an update by running Chrome and navigating to the Help > About page (click the ‘three dots’ icon at the top right).
Opera 40.0.2308.81
A few bug fixes and an update for the Chromium engine comprise the changes in Opera 40.0.2308.81. The Chrome 40 change log lists thirteen total changes, including fixes for some annoying address bar and bookmark issues. There are no security fixes in this release.
 boot13
boot13