 If you’re old enough to remember the browser wars of the 1990s, you probably remember that Microsoft got into trouble for pushing their web browser, Internet Explorer, using tactics tied to the dominance of Windows.
If you’re old enough to remember the browser wars of the 1990s, you probably remember that Microsoft got into trouble for pushing their web browser, Internet Explorer, using tactics tied to the dominance of Windows.
Competitors were less than thrilled with Microsoft’s tactics. In 1998, an anti-trust suit was launched by the US Department of Justice against Microsoft, alleging that Microsoft was using unfair tactics, in particular by embedding Internet Explorer into Windows, making it difficult to remove.
Microsoft argued that Internet Explorer was a core part of the operating system, and could not be easily excised from Windows. This didn’t help their case much, as you can imagine.
The court agreed with the DOJ, recommending that Microsoft be broken into two organizations, one for Windows and the other for applications like Internet Explorer. After appeals, the final settlement required Microsoft to share its API (Application Programming Interface) documentation with third party companies. The idea was to remove any head start Microsoft would have in developing changes to its web browser based on technology advancements.
The DOJ did not require Microsoft to change any of its code or prevent Microsoft from tying other software with Windows in the future.
Microsoft’s tactics this time around
Fast forward to today, and Microsoft is again using questionable tactics in its fight for web browser dominance. This time around, with Internet Explorer soon to be discontinued, the browser in question is Edge (the newer, Chromium-based version).
Microsoft recently published a small support article about the new version of Edge, presumably in response to user questions. In part, it states: “The new version of Microsoft Edge is included in a Windows system update, so the option to uninstall it or use the legacy version of Microsoft Edge will no longer be available.”
So, once again, Microsoft is apparently trying to use its dominance in the desktop operating system market to push its web browser on people.
It’s hard to predict whether this tactic will actually help Edge, or whether anyone will care enough to claim antitrust activity again. I like to think people are generally somewhat better informed, and recognize that there are other, better web browsers than Edge.
UPDATE 2020Sep12: Microsoft has revised the wording of the support article about this, but the new version sounds like more of the same weak arguments they used in the 1990s:
Because Windows supports applications that rely on the web platform, our default web browser is an essential component of our operating system and can’t be uninstalled.
Windows users can download and install other browsers and change their default browser at any time.
Giant corporations trying to sound innocent when caught in their shenanigans is just embarassing.
 Is it just me, or is Microsoft actually getting worse at this? It seems that every month there are more horror stories about problems caused by MS software updates. Given that Microsoft is still pushing hard for all Windows updates to happen automatically, this is very troubling.
Is it just me, or is Microsoft actually getting worse at this? It seems that every month there are more horror stories about problems caused by MS software updates. Given that Microsoft is still pushing hard for all Windows updates to happen automatically, this is very troubling. boot13
boot13 I just received a text message from someone pretending to be a representative of the Liberal Party of Canada.
I just received a text message from someone pretending to be a representative of the Liberal Party of Canada.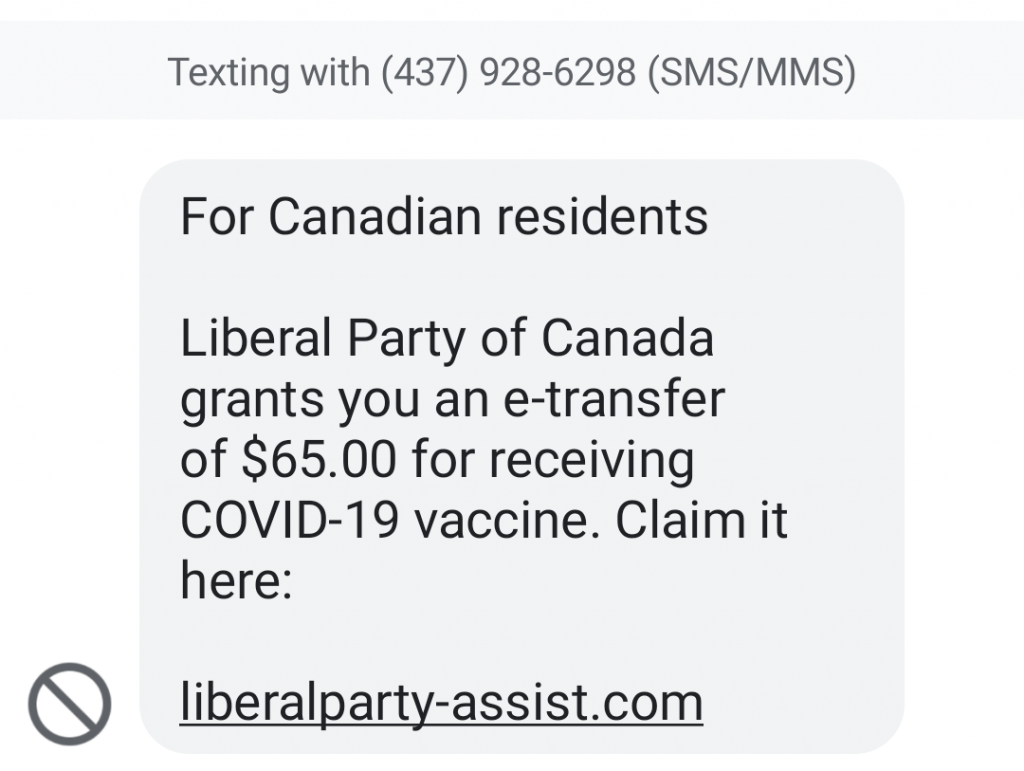
 If you’re old enough to remember the
If you’re old enough to remember the  Canadians: if you’ve tried to access your CRA accounts recently, you probably noticed that you can no longer log in. That’s because normal access has been disabled while the CRA works to undo the damage caused by two recent attacks on their services.
Canadians: if you’ve tried to access your CRA accounts recently, you probably noticed that you can no longer log in. That’s because normal access has been disabled while the CRA works to undo the damage caused by two recent attacks on their services. With Windows 10, Microsoft shifted a lot of their testing to users, through the
With Windows 10, Microsoft shifted a lot of their testing to users, through the