There’s not much to talk about in Chrome 55.0.2883.87. The change log lists about thirteen actual changes, but none of those are related to security and they’re all relatively minor.
All posts by jrivett
Mr. Robot’s realistic depiction of hacking
As I read Cory Doctorow’s recent Technology Review post, “Mr. Robot Killed the Hollywood Hacker“, I found myself nodding my head enthusiastically. Anyone who knows much about computers and watches Mr. Robot will have noticed that the show’s depiction of hacking is very different from what we usually see on TV and in movies. The user interface is a text console. Everything is done with arcane text commands. Nothing is flashing, except the prompt. In other words, it’s accurate.
For as long as computers have been shown in movies and TV, they have been depicted as flashy, noisy, exploding, and otherwise utterly fanciful, almost magical devices. Hollywood obviously took one look at reality and collectively said “no way, that’s boring as hell.” So the vast majority of computer depictions in movies and TV are some art director’s crazy fantasy of how a computer should look.
I long ago stopped complaining about this. Nobody wants to listen to me drone on about how unrealistic a computer is in some TV show. Now, I just allow myself to be amused. I told myself that this was just harmless hyperbole, a layer of pizazz added onto reality to make it more entertaining.
But Doctorow makes an interesting point: the traditional depiction of computers by Hollywood isn’t as harmless as it may seem.
The 1983 film WarGames is about a high school kid who accidentally hacks into a military computer and almost starts a global thermonuclear war. There were – and still are – a lot of reasons why this is an unlikely scenario, but hey, this is entertainment. A lot of people saw the film, and most enjoyed it, including me. One of the least realistic parts of the film shows the WOPR computer smoking and burning when it becomes overloaded. Real computers just stop working when they’re overtaxed. Anyway, I didn’t mind the silliness; it’s all good fun, right?
Wrong. Apparently, Wargames got some people in Washington worried about whether a high school kid really could hack into military systems and start a war. In 1984, one year after the release of WarGames, the US Congress passed the Computer Fraud and Abuse Act (CFAA), which made activities related to hacking illegal. The legislation is ill-defined, and overly-broad, and it’s widely seen as pointlessly destructive. It contributed to the suicide of Aaron Swartz, who was being charged with crimes related to the CFAA.
The next time you’re watching a TV show or movie, and see an inaccurate depiction of something, ask yourself: “is this really just a harmless Hollywood convenience?”
Vivaldi 1.5.658.56
Earlier this week a minor update was released for Vivaldi. A new update mechanism was used (for the first time) to distribute this version to existing Vivaldi clients; according to the release notes for version 1.5.658.56, this reduced the size of the download to 323 kilobytes. The full download for Vivaldi 1.5.658.56 is 38.5 megabytes.
The update itself includes a few minor bug fixes, none related to security.
Chrome 55.0.2883.75
A new version of Chrome fixes at least thirty-six security issues in the browser. Aside from listing the vulnerabilities addressed, the release announcement says only that Chrome 55.0.2883.75 “contains a number of fixes and improvements”. You’ll have to read the change log to figure out what else is different. Sadly, the full change log is another one of those browser-killing monstrosities, with almost 10,000 changes listed. Don’t click that link if you have an older computer.
New, critical Firefox zero-day
If you’re a Firefox user, you might want to think about using a different browser for the next day or so. Researchers have discovered a critical vulnerability that has yet to be patched. Mozilla is working on a fix but there’s no word on when it will be available.
Update 2016Nov30: Mozilla just released Firefox 50.0.2, which includes a fix for this vulnerability. Mozilla posted about this as well.
Firefox 50.0.1 fixes one critical security issue
There’s a critical security vulnerability in Firefox 49 and 50, and Mozilla just released Firefox 50.0.1 to address it. Which is great, except for one thing: the total lack of anything resembling an announcement.
Yes, Firefox can be configured to update itself or alert you when an update is available, but that setting can also be disabled completely. Worse, it can take days for Firefox’s internal update checker to detect that there’s a new version.
I discovered the new version by way of a post on the US-CERT site.
Opera 41.0.2353.69
Version 41.0.2353.69 of Opera upgrades the browser’s Chromium engine, and fixes one ‘nasty’ crashing problem involving dragged bookmarks (change log).
Vivaldi 1.5
A new version of alternative web browser Vivaldi fixes a load of bugs, improves reader mode, and adds the ability to control home lighting.
Wait, what? Home lighting control? That’s right, Vivaldi 1.5 sports a feature that’s unlikely to have been on anyone’s wish list for their web browser. From the announcement: “Selecting which lights Vivaldi should control, the browser will synchronize your physical surroundings with the color of the web. This opens the door to a thrilling direction.” Apparently the Vivaldi developers are oblivious to the many serious security issues related to IoT devices, including the Philips Hue light bulbs on which this feature depends.
More usefully, Vivaldi 1.5 makes big improvements to tab and bookmark functionality, which in previous versions were at least partially broken in various, random ways. Version 1.5 seems to have addressed all of the remaining tab and bookmark issues.
Vivaldi 1.5 also includes changes to its update mechanism, and will now only download changes (not the entire browser) when updating itself. Presumably the Vivaldi developers noticed Microsoft was doing this for Windows 10 and decided to follow along. It’s a welcome change, but not exactly groundbreaking.
The official announcement post for Vivaldi 1.5 includes a list of all the changes. None of them seem to be related to security.
SHA-1 deprecation coming soon
SHA-1 (Secure Hash Algorithm 1) is still used by some web sites to encrypt their traffic. Starting in early 2017, most web browsers will start displaying scary-looking warnings when anyone tries to visit sites using SHA-1.
Like this one in Edge:
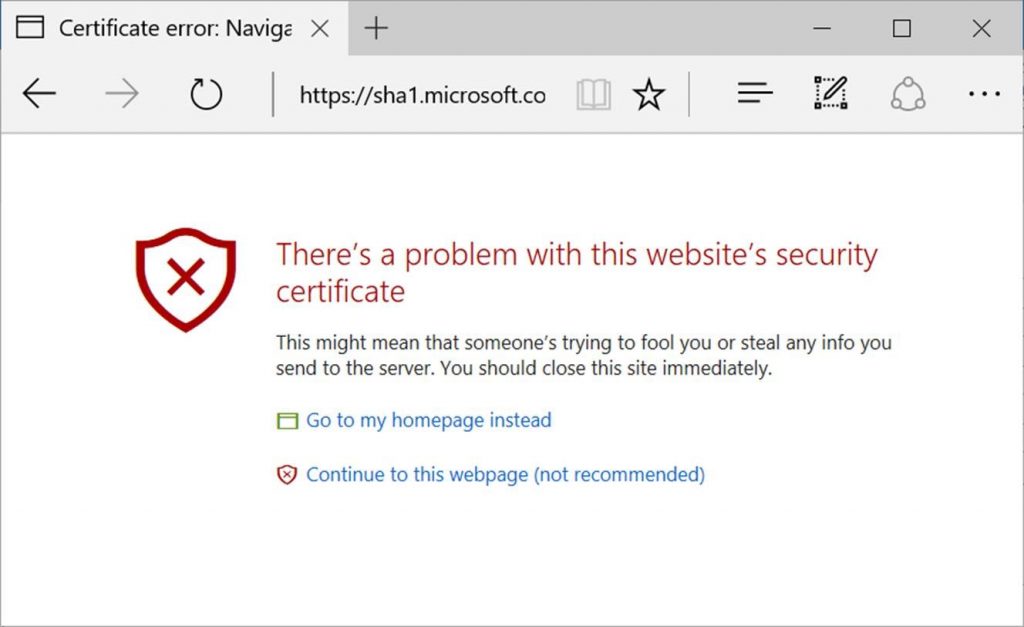
SHA-1 deprecation announcements
Microsoft
(From a post on the Microsoft Edge blog.)
Starting on February 14th, 2017, Microsoft Edge and Internet Explorer 11 will prevent sites that are protected with a SHA-1 certificate from loading and will display an invalid certificate warning. Though we strongly discourage it, users will have the option to ignore the error and continue to the website.
Mozilla
From a post on the Mozilla security blog.
In early 2017, Firefox will show an overridable “Untrusted Connection” error whenever a SHA-1 certificate is encountered that chains up to a root certificate included in Mozilla’s CA Certificate Program. SHA-1 certificates that chain up to a manually-imported root certificate, as specified by the user, will continue to be supported by default; this will continue allowing certain enterprise root use cases, though we strongly encourage everyone to migrate away from SHA-1 as quickly as possible.
From a post on the Google security blog.
We are planning to remove support for SHA-1 certificates in Chrome 56, which will be released to the stable channel around the end of January 2017. The removal will follow the Chrome release process, moving from Dev to Beta to Stable; there won’t be a date-based change in behaviour.
Firefox 50 fixes 27 security bugs
Firefox users are advised to make sure it’s up to date: version 50 — released yesterday — addresses at least twenty-seven security vulnerabilities. To find out what version you’re running, click the ‘hamburger’ menu icon at the top right, click the question mark icon, then click ‘About Firefox’.
Aside from the security fixes, there’s not much of interest in Firefox 50. The release notes provide additional information.
 boot13
boot13