A new version of Chrome was made available today. Included in version 26.0.1410.64 is a new version of Flash (11.7), and some stability improvements.
Category Archives: Adobe
Flash 11.7 released
Today, Adobe announced the latest version of Flash, 11.7.
The new version includes security improvements related to Firefox, and fixes several bugs.
The changes in Flash 11.7 will find their way into Internet Explorer 10 and Google Chrome in the near future, in the form of separate updates for those programs.
Flash 11.6.602.180 released
A new version of Flash was announced today. Version 11.6.602.180 fixes several security (and other) bugs and adds a few new features. The security issues are described in the associated security bulletin: APSB13-09. The rest of the changes are covered in the release notes for 11.6.602.180.
Google Chrome, Flash, and ‘component updater’
A few days ago, I posed a series of questions about Flash in Chrome. Since then, I’ve done some digging, and I’m now able to answer most of those questions.
- Q: What is the ‘component updater’?
A: It’s a process used by Chrome to silently and automatically update certain specific components of the browser. The new, integrated Flash component falls into that category, so Flash in Chrome is updated automatically and without any notification to the user. When new versions of Chrome are released, Google may or may not refer to Flash updates in the release notes. - Q: How does the component updater affect the version number of Chrome in Windows?
A: It doesn’t. Component updates are distinct from new versions of the browser itself. You can, however, find the versions of Chrome’s components by browsing to special addresses in Chrome, as follows:- chrome://plugins/ – lists all plugins, along with their versions, including the integrated Flash.
- chrome://flash/ – shows details of the integrated Flash component, including its version.
- chrome://version/ – shows a version summary for Chrome and its major components, including the integrated Flash.
- Q: Has Flash been updated in my version of Chrome or not?
A: You can’t depend on Google to announce new versions of the integrated Flash, regardless of whether the new version is packaged along with a new version of Chrome, or updated separately via the component updater. Use one of the special URLs listed above to check the version you’re using. - Q: How can I determine what version of Flash is running in Chrome?
A: Use one of the special URLs listed above. - Q: What is “Windows Standalone Enterprise”?
A: This remains a mystery. The Chrome release channels page doesn’t mention it. Perhaps it’s only available to enterprise (corporate) clients. Or possibly the Chrome announcement that referred to this channel was in error. In any case, you can’t really depend on Google’s announcements to mention new Flash versions; use one of the specials URLs above, along with Flash announcements from Adobe, to determine what version of Flash you have, and what version you need.
More security updates for Adobe Flash
On February 26, Adobe announced version 11.6.602.171 of the Flash player. As usual, Adobe says: “These updates address vulnerabilities that could cause a crash and potentially allow an attacker to take control of the affected system.” The technical details are available in Adobe Security Bulletin APSB13-08.
Microsoft simultaneously announced a Flash update for Internet Explorer 10 on Windows 8, which will be delivered via Windows Update.
Google will no doubt release a new version of Chrome that includes the Flash updates in the next day or so.
Anyone who uses Flash in their web browser should install the appropriate update as soon as possible. That includes anyone who uses Youtube. So basically just about everyone.
Updates for Adobe Reader
As expected, Adobe has announced updates for its Reader and Acrobat software to address recently-revealed security vulnerabilities. The full technical details are available in the related security bulletin.
Adobe Reader software currently being exploited
There’s a brief announcement on the Adobe Product Security Incident Response Team (PSIRT) Blog stating that Adobe is looking into reports of a new exploit for their Reader software. No further details are provided. Since this exploit is apparently being seen in the wild, we recommend extreme caution when opening PDF documents from unknown or untrusted sources. Better yet, switch to a different PDF reader like Foxit, thereby avoiding the dangers inherent in using Adobe Reader.
Update: Ars Technica has the details. Apparently the vulnerability was reported by the security company FireEye, and attacks based on the vulnerability have been seem in the wild. Further, the vulnerability is important because security in version 11 of the Reader software was supposedly much more difficult to circumvent.
Update 2: There’s a new post on the Security Advisory blog for Adobe Reader and Acrobat that covers this issue.
Update 3: Ars Technica points out that Adobe Reader 11 would protect users from this vulnerability, if its security settings were actually enabled by default (which they aren’t). On learning this, I immediately made the required changes to my installation of Reader, enabling Protected View. Check the bottom of this post for the procedure.
Update 4: Adobe announced that updates for the vulnerabilities in Reader will be made available some time during the coming week.
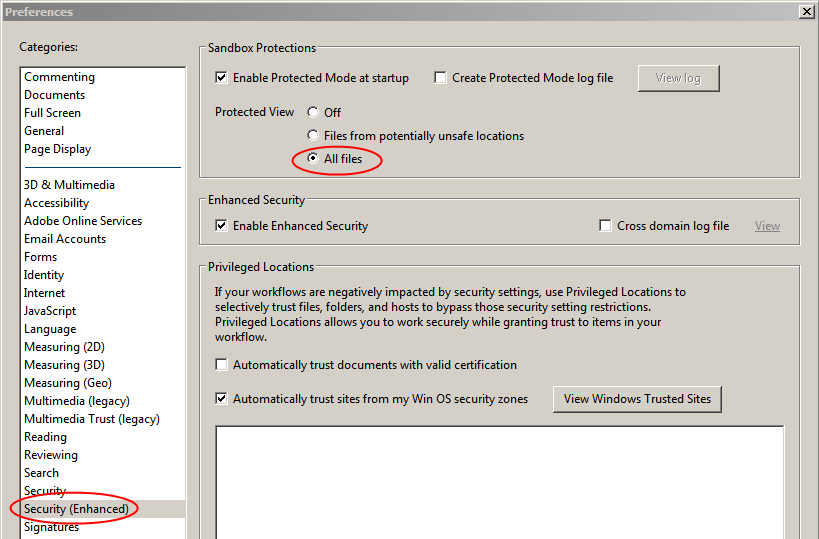
Enabling Protected View in Adobe Reader 11
- Start Adobe Reader.
- From the menu, select Edit > Preferences.
- Select Security (Enhanced) from the list on the left.
- In the Sandbox Protections section at the top, make sure that the setting for Protected View is All files.
- Click OK.
New versions of Adobe Flash
Yesterday Adobe announced version 11.6 of the Flash player. All platforms are affected.
Version 11.6 includes several security fixes, as well as some new features.
The technical details are available in the release notes and in the related security bulletin from Adobe: APSB13-05.
Anyone using Flash (e.g. Youtube) should install the new version as soon as possible.
Flash player update fixes serious security issues
Yesterday, Adobe announced an update for Flash that fixes specific security issues that are currently being exploited on the web.
Anyone who uses Flash should install the update as soon as possible.
The new version for Windows XP, Vista and 7 is 11.5.502.149. The new version for Windows 8 (available as an update from Microsoft) is 11.3.379.14.
Plugins will be safer in future versions of Firefox
Presumably in response to the recent flood of Java vulnerabilities, the developers of Firefox (Mozilla) will be adding a new layer of security to all plugins, including the notororiously insecure Java, Flash and Adobe Reader.
Essentially, the new security will consist of additional prompts when plugins are triggered. So when a web site tries to run Java code, Firefox will prompt you to make sure you really want to allow the plugin to activate and run the Java code. You will be able to control which plugins and sites are affected.
Oracle/Sun recently made similar changes to Java itself, in an attempt to improve the overall safety of Java in web browsers. However, as security researcher Adam Gowdiak points out, those changes are ineffective: Java code can still run silently, bypassing the new safeguards. He writes:
… unsigned Java code can be successfully executed on a target Windows system regardless of the four Java Control Panel settings …
Our Proof of Concept code … has been successfully executed in the environment of [the] latest Java SE 7 Update 11 (JRE version 1.7.0_11-b21) under Windows 7 … and with “Very High” Java Control Panel security settings.That said, recent … security “improvements” to Java SE 7 software don’t prevent silent exploits at all. Users that require Java content in the web browser need to rely on a Click to Play technology implemented by several web browser vendors in order to mitigate the risk of a silent Java Plugin exploit.
 boot13
boot13