SHA-1 (Secure Hash Algorithm 1) is still used by some web sites to encrypt their traffic. Starting in early 2017, most web browsers will start displaying scary-looking warnings when anyone tries to visit sites using SHA-1.
Like this one in Edge:
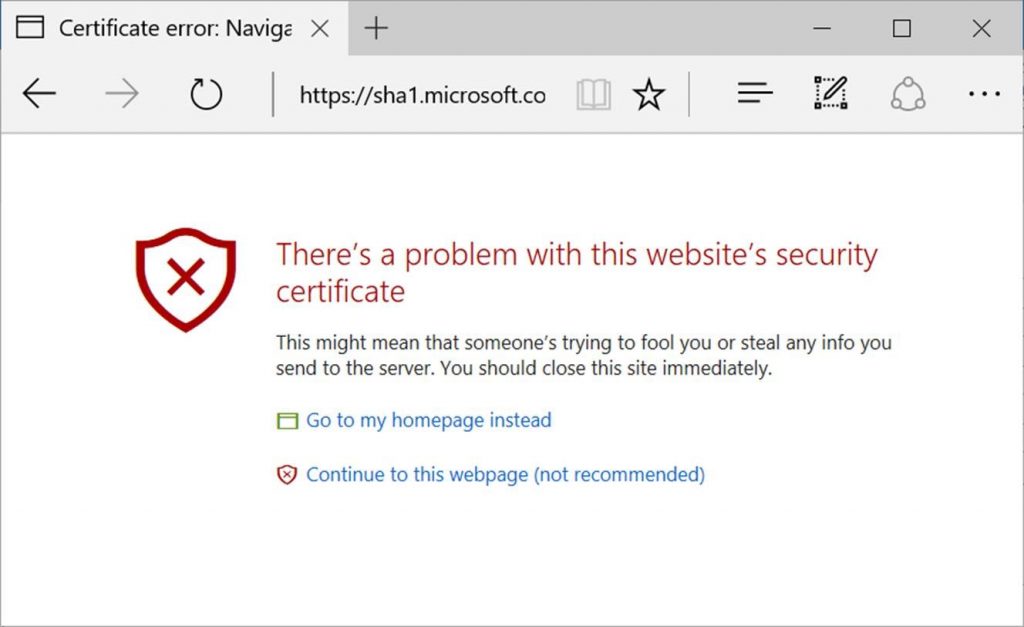
SHA-1 deprecation announcements
Microsoft
(From a post on the Microsoft Edge blog.)
Starting on February 14th, 2017, Microsoft Edge and Internet Explorer 11 will prevent sites that are protected with a SHA-1 certificate from loading and will display an invalid certificate warning. Though we strongly discourage it, users will have the option to ignore the error and continue to the website.
Mozilla
From a post on the Mozilla security blog.
In early 2017, Firefox will show an overridable “Untrusted Connection” error whenever a SHA-1 certificate is encountered that chains up to a root certificate included in Mozilla’s CA Certificate Program. SHA-1 certificates that chain up to a manually-imported root certificate, as specified by the user, will continue to be supported by default; this will continue allowing certain enterprise root use cases, though we strongly encourage everyone to migrate away from SHA-1 as quickly as possible.
From a post on the Google security blog.
We are planning to remove support for SHA-1 certificates in Chrome 56, which will be released to the stable channel around the end of January 2017. The removal will follow the Chrome release process, moving from Dev to Beta to Stable; there won’t be a date-based change in behaviour.
 boot13
boot13