Oracle/Sun has announced that additional security-related updates for Java will be made available on February 19. The emergency updates released on February 1 were originally scheduled to be released with the upcoming updates on February 19. Stay tuned.
Category Archives: Security
aka infosec
Adobe Reader software currently being exploited
There’s a brief announcement on the Adobe Product Security Incident Response Team (PSIRT) Blog stating that Adobe is looking into reports of a new exploit for their Reader software. No further details are provided. Since this exploit is apparently being seen in the wild, we recommend extreme caution when opening PDF documents from unknown or untrusted sources. Better yet, switch to a different PDF reader like Foxit, thereby avoiding the dangers inherent in using Adobe Reader.
Update: Ars Technica has the details. Apparently the vulnerability was reported by the security company FireEye, and attacks based on the vulnerability have been seem in the wild. Further, the vulnerability is important because security in version 11 of the Reader software was supposedly much more difficult to circumvent.
Update 2: There’s a new post on the Security Advisory blog for Adobe Reader and Acrobat that covers this issue.
Update 3: Ars Technica points out that Adobe Reader 11 would protect users from this vulnerability, if its security settings were actually enabled by default (which they aren’t). On learning this, I immediately made the required changes to my installation of Reader, enabling Protected View. Check the bottom of this post for the procedure.
Update 4: Adobe announced that updates for the vulnerabilities in Reader will be made available some time during the coming week.
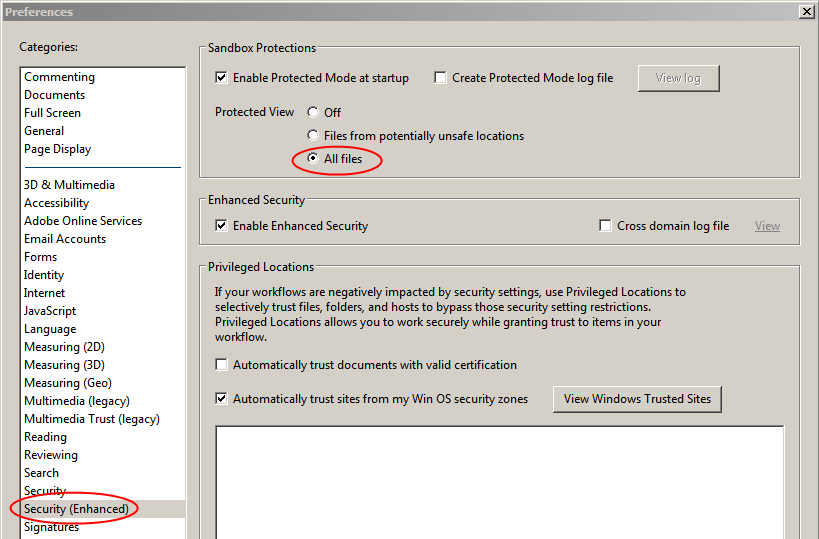
Enabling Protected View in Adobe Reader 11
- Start Adobe Reader.
- From the menu, select Edit > Preferences.
- Select Security (Enhanced) from the list on the left.
- In the Sandbox Protections section at the top, make sure that the setting for Protected View is All files.
- Click OK.
New version of Chrome
Version 24.0.1312.70 of Google’s web browser contains the latest version of Adobe Flash.
Update: Something funny going on here. The announcement linked above states that version 24.0.1312.70 is actually for the Linux platform. It goes on to say: “This release contains an update to Flash (11.6.602.167). This Flash update has been pushed to Windows, Mac, and Chrome Frame platforms through component updater.” But what is the ‘component updater’, and how will it affect the version number of Chrome in Windows? There’s nothing on the Chrome support site about it. My own Chrome installation reports itself as being up to date at version 24.0.1312.57. Has Flash been updated in my installation or not? How can I determine what version of Flash is running in Chrome? Comments below the announcement linked above show other users similarly confused. Meanwhile, another new version was announced on Feb 14: “The Stable channel has been updated to 24.0.1312.71 for Windows Standalone Enterprise. This build contains an updated Flash (11.6.602.167).” That version at least seems to be targeted at Windows, but what is “Windows Standalone Enterprise”? It contains the same version of Flash as 24.0.1312.70, but again my version of Chrome reports that it is up to date at 24.0.1312.57. Not much we can do at this point except wait for Google to sort out this mess.
New versions of Adobe Flash
Yesterday Adobe announced version 11.6 of the Flash player. All platforms are affected.
Version 11.6 includes several security fixes, as well as some new features.
The technical details are available in the release notes and in the related security bulletin from Adobe: APSB13-05.
Anyone using Flash (e.g. Youtube) should install the new version as soon as possible.
Microsoft teams up with Symantec to take down another botnet
Microsoft and Symantec, working with law enforcement authorities in the US and Spain, have disabled another botnet. The Bamital botnet first appeared in 2009, and at its height, included as many as 1.8 million computers.
User computers became infected with the Bamital malware through drive-by web-based infections (often from porn sites) and corrupted software downloads.
Infected computers were used to generate revenue for the perpetrators by generating or redirecting traffic to specific web sites.
Flash player update fixes serious security issues
Yesterday, Adobe announced an update for Flash that fixes specific security issues that are currently being exploited on the web.
Anyone who uses Flash should install the update as soon as possible.
The new version for Windows XP, Vista and 7 is 11.5.502.149. The new version for Windows 8 (available as an update from Microsoft) is 11.3.379.14.
Latest SANS: Ouch! – Email Phishing Attacks
This month’s Ouch! newsletter (PDF) from SANS is about email ‘phishing’ attacks. According to Wikipedia,
Phishing is the act of attempting to acquire information such as usernames, passwords, and credit card details (and sometimes, indirectly, money) by masquerading as a trustworthy entity in an electronic communication.
It’s a worthwhile read, and describes different types of phishing attacks and what you can do to protect yourself from them.
Massive Java security update
Oracle/Sun has released update 13 for Java 7 (Java 7u13).
The update was originally scheduled for release on February 19, but given all the recent security issues, Oracle decided to get the latest patch out there as soon as possible.
The update includes fifty bug and security fixes. The issues addressed are listed on the associated Critical Patch Update Advisory. Oddly, the update version (7u13) is never mentioned once on that lengthy page.
Recommendations:
- If you use Java, update it ASAP.
- Don’t depend on the Java auto-updater to update Java: do it manually.
- Don’t assume Java is now safe. Until security researchers like Adam Gowdiak give Java 7u13 a thumbs-up, assume it’s still vulnerable.
- Disable Java plugins in your web browser unless you have no choice.
- Continue to be extremely careful when browsing the web.
All about malware
Ars Technica just posted an excellent introduction to malware. The post talks about all the major categories of malware currently in the wild, and lists key indicators that your computer may be infected. Recommended reading for anyone not already well versed in current malware trends.
Plugins will be safer in future versions of Firefox
Presumably in response to the recent flood of Java vulnerabilities, the developers of Firefox (Mozilla) will be adding a new layer of security to all plugins, including the notororiously insecure Java, Flash and Adobe Reader.
Essentially, the new security will consist of additional prompts when plugins are triggered. So when a web site tries to run Java code, Firefox will prompt you to make sure you really want to allow the plugin to activate and run the Java code. You will be able to control which plugins and sites are affected.
Oracle/Sun recently made similar changes to Java itself, in an attempt to improve the overall safety of Java in web browsers. However, as security researcher Adam Gowdiak points out, those changes are ineffective: Java code can still run silently, bypassing the new safeguards. He writes:
… unsigned Java code can be successfully executed on a target Windows system regardless of the four Java Control Panel settings …
Our Proof of Concept code … has been successfully executed in the environment of [the] latest Java SE 7 Update 11 (JRE version 1.7.0_11-b21) under Windows 7 … and with “Very High” Java Control Panel security settings.That said, recent … security “improvements” to Java SE 7 software don’t prevent silent exploits at all. Users that require Java content in the web browser need to rely on a Click to Play technology implemented by several web browser vendors in order to mitigate the risk of a silent Java Plugin exploit.
 boot13
boot13