 I just discovered an interesting and useful web site: Should I Block Ads?
I just discovered an interesting and useful web site: Should I Block Ads?
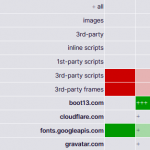
Created by Michael Howell, it’s collection of information that can be helpful in deciding whether to install an ad blocker in your web browser. It also provides ad-blocker recommendations for various platforms and browsers.
Michael’s analysis addresses all of the concerns I’ve had with web-based advertising, and confirms my choice to install and use uBlock Origin in Firefox, my primary web browser.
If you’re considering installing an ad blocker in your web browser, keep in mind that there can be a bit of a learning curve, and that blocking ads can cause some web sites to stop working. Blocking web ads usually ends up being an ongoing process; don’t expect it to be a magic bullet.
There are of course arguments against ad-blocking. Just keep in mind that a site owner always has the option of placing hand-crafted advertisements on their site; as long as they don’t use Javascript and are not associated with known advertising networks, they will not be blocked.
 boot13
boot13 We’re in the middle of a pandemic, but that’s no excuse to leave software unpatched. There’s certainly been no reduction in the rate at which vulnerabilities and exploits are being discovered.
We’re in the middle of a pandemic, but that’s no excuse to leave software unpatched. There’s certainly been no reduction in the rate at which vulnerabilities and exploits are being discovered. Adobe once again tags along this month, with new versions of Reader and Acrobat. Most people use the free version of Reader, officially known as Acrobat Reader DC. The new version,
Adobe once again tags along this month, with new versions of Reader and Acrobat. Most people use the free version of Reader, officially known as Acrobat Reader DC. The new version,  Announced on May 5,
Announced on May 5,  At this point, most folks probably don’t need Java. Which is good, because it’s still a target for malicious hackers. If you don’t actually need Java, it’s a good idea to remove it completely from your computers.
At this point, most folks probably don’t need Java. Which is good, because it’s still a target for malicious hackers. If you don’t actually need Java, it’s a good idea to remove it completely from your computers. A new version of Chrome addresses thirty-two security issues in previous versions.
A new version of Chrome addresses thirty-two security issues in previous versions.